VPC 101: Mastering the Foundations of AWS Virtual Private Clouds

Amazon Web Services (AWS) Virtual Private Cloud (VPC) is a foundational service that allows users to create isolated networks within the AWS cloud. This comprehensive guide will help you master the basics of VPCs, understand their importance, explore various use cases, and provide detailed step-by-step instructions for setting up and managing your VPCs.
What is an AWS Virtual Private Cloud (VPC)?
An AWS VPC is a virtual network that closely resembles a traditional network you might operate in your own data center, with the benefits of scalable infrastructure provided by AWS. A VPC enables you to launch AWS resources, such as Amazon EC2 instances, in a logically isolated section of the AWS cloud.
Key Features of AWS VPC
1. Isolation
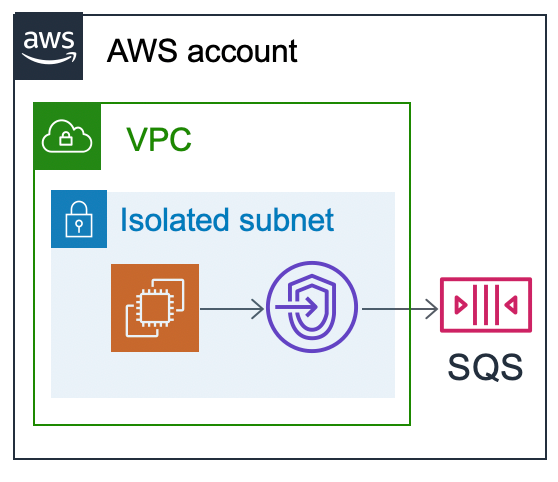
- VPCs create a logically isolated network environment within the AWS cloud. This means your resources, like EC2 instances and databases, are separated from other users' resources.
- This isolation enhances security by preventing unauthorized access to your resources from outside your VPC. You have more control over who and what can access your data.
2. Subnets
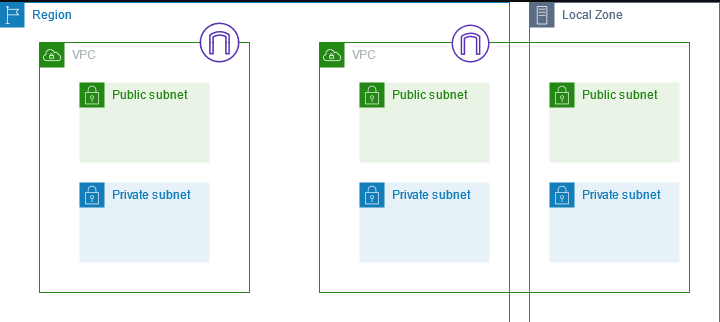
- A VPC can be further segmented into subnets, which are smaller portions of the IP address range you define for your VPC.
- Subnets can be created within specific Availability Zones (AZs) for redundancy and fault tolerance. If one AZ has an outage, resources in other AZs can remain operational.
- You can designate subnets as either public or private:
- Public subnets: Have a route to the internet gateway, allowing resources launched in these subnets to communicate directly with the internet.
- Private subnets: Do not have a direct route to the internet gateway, making them ideal for resources that shouldn't be publicly accessible.
3. Route Tables
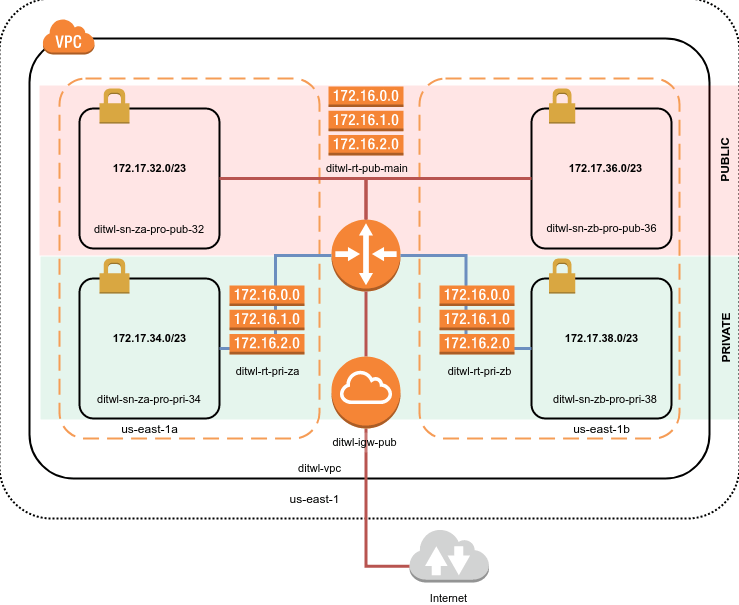
- Route tables act like traffic maps within your VPC, directing traffic flow to the appropriate destination.
- Each subnet is associated with a route table that determines how network traffic is routed in and out of the subnet.
- You can configure routes to the internet gateway for public internet access, or to other VPCs or AWS services using VPC endpoints.
4. Internet Gateways
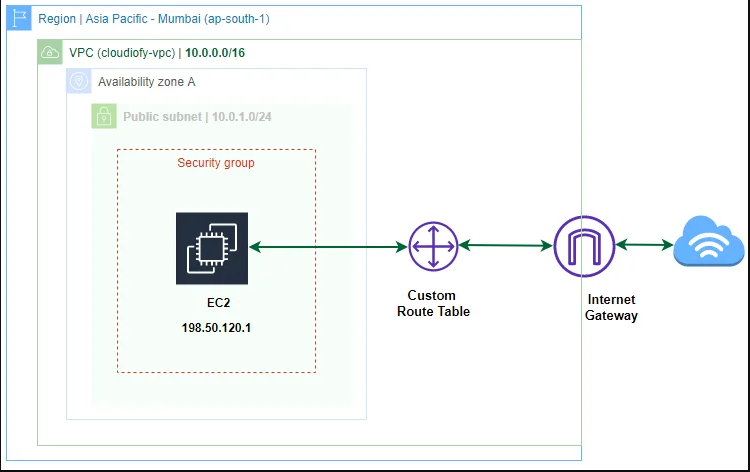
- An internet gateway acts as the entry and exit point for internet traffic within your VPC.
- By attaching an internet gateway to your VPC, you enable resources in public subnets to communicate with the internet.
- You can have only one internet gateway per VPC.
5. Security Groups and Network ACLs
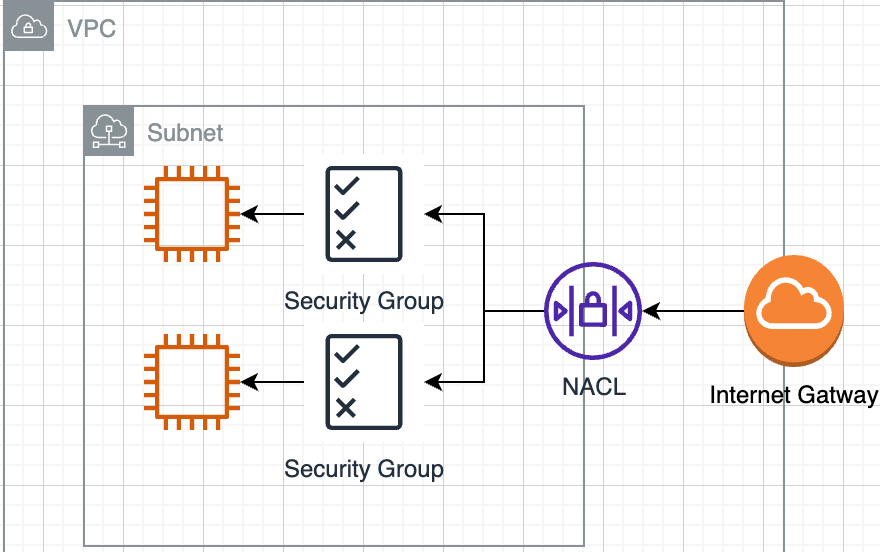
- Security groups and Network Access Control Lists (NACLs) act as firewalls, controlling inbound and outbound traffic at different levels of your VPC:
- Security Groups: Are stateful firewalls attached to individual EC2 instances. They define rules that allow or deny specific traffic flows to and from the instance.
- Network ACLs: Are stateless firewalls attached to subnets. They apply to all traffic entering or leaving the subnet, regardless of the specific instance.
6. VPC Peering:
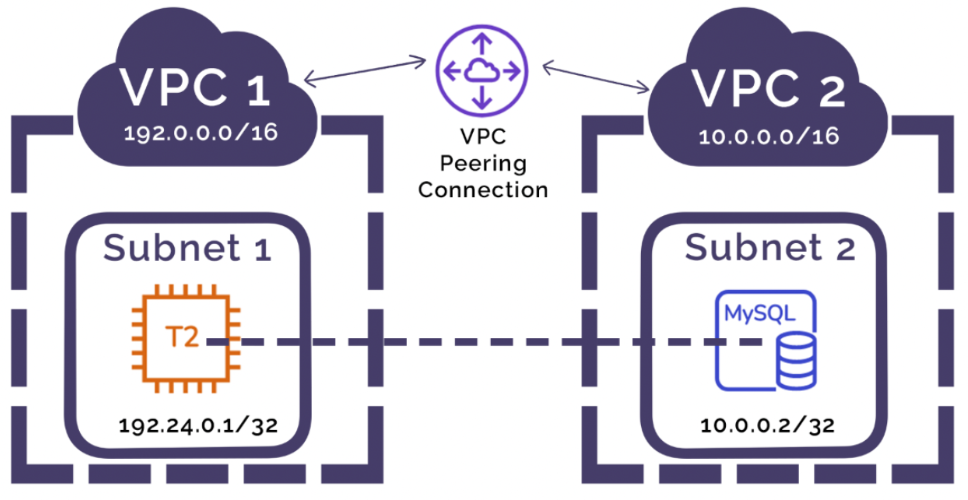
Enables private connectivity between VPCs within the same AWS account or across different accounts and regions. This allows resources in separate VPCs to communicate securely without traversing the internet.
7. AWS Direct Connect:
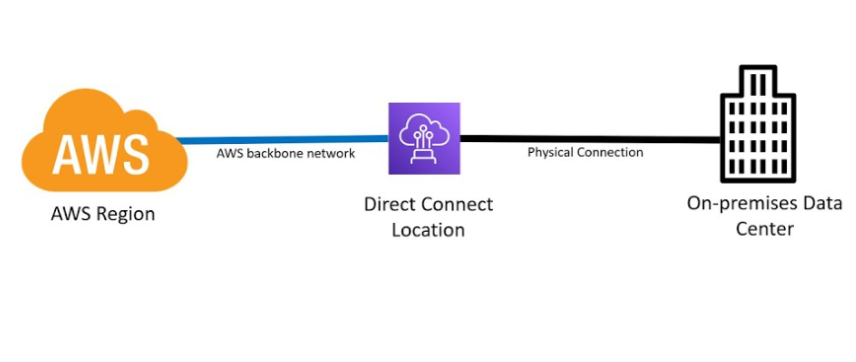
Provides a dedicated network connection between your on-premises network and your VPC. This offers a more consistent and reliable connection compared to using the internet.
8. VPN Connections:
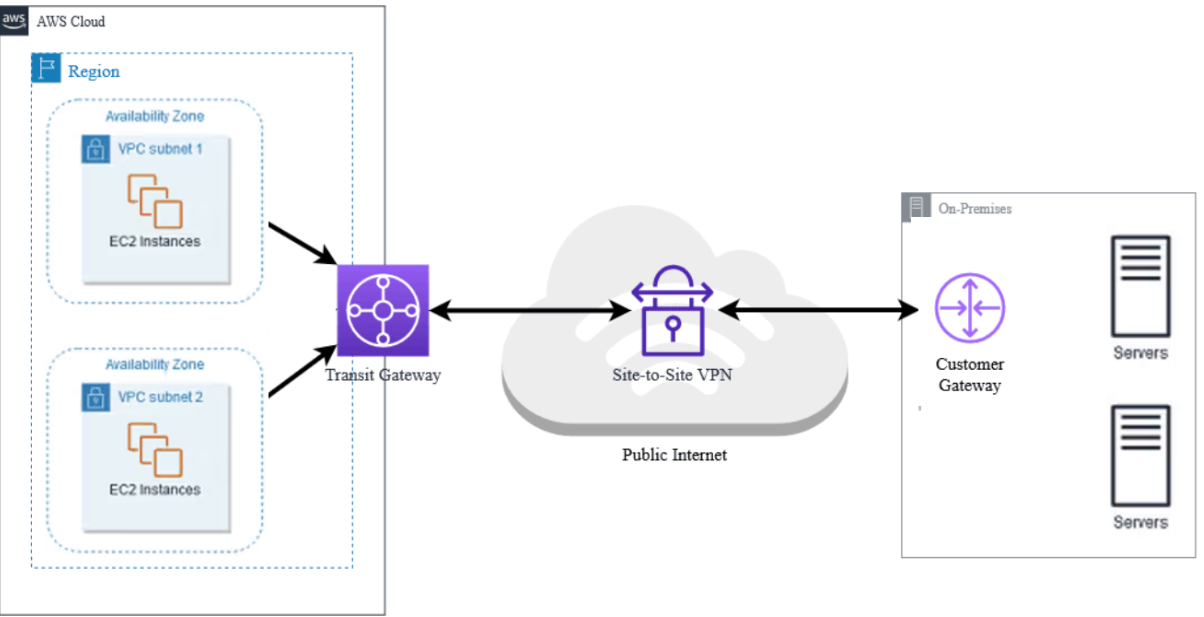
Create secure tunnel connections between your VPC and your on-premises network using industry-standard VPN protocols.
9. VPC Endpoints:
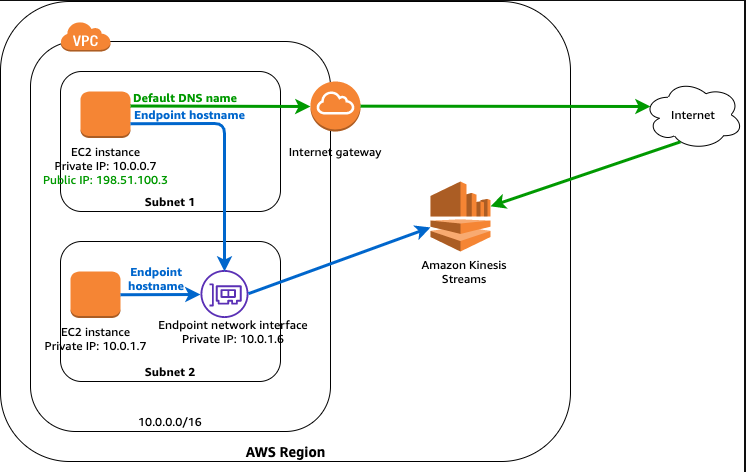
Allow private connectivity between your VPC and specific AWS services without requiring an internet gateway or NAT instance. This keeps your traffic within the AWS network for increased security and performance.
10. Transit Gateway:
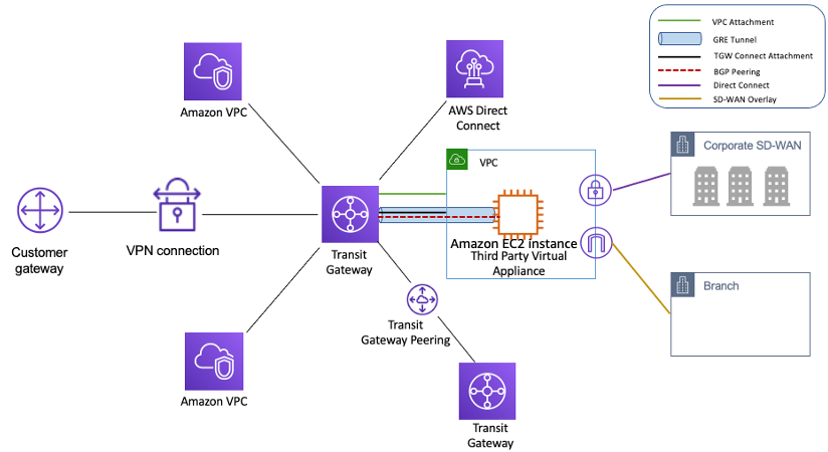
Acts as a central hub for routing traffic between multiple VPCs and AWS services. It simplifies managing complex network architectures with many VPCs.
Common Use Cases
Hosting Web Applications
- Security: By leveraging VPC features like security groups and network ACLs, you can restrict access to your web application servers only from authorized sources. This reduces the risk of attacks and data breaches.
- Scalability: VPC allows you to launch web servers in auto-scaling groups within specific subnets. This enables automatic scaling of your web application based on traffic demands, ensuring high availability and performance.
- Multi-Tier Architecture: You can design your web application with separate tiers (e.g., web server, application server, database) in different subnets. This allows you to control traffic flow between tiers and improve security by keeping the database tier private. I've previously written about building multi-tier architectures and you can find it here.
- Load Balancing: VPC integrates seamlessly with Elastic Load Balancing (ELB) to distribute traffic across multiple web servers, ensuring high availability and preventing a single server failure from impacting user experience.
Hybrid Cloud Architectures
- Secure Connectivity: VPC offers options like VPN connections and AWS Direct Connect to establish secure and private connections between your on-premises network and your VPC in the cloud. This allows seamless communication between resources in both environments.
- Data Governance: By keeping sensitive data within your VPC and controlling access through security groups and network ACLs, you can comply with data security regulations and maintain data residency requirements.
- Centralized Management: You can leverage AWS tools and services to manage resources across your on-premises network and your VPC in a unified way, simplifying overall administration.
- Phased Migration: VPC allows for a phased migration of your IT infrastructure to the cloud. You can start by migrating specific applications or workloads while keeping critical systems on-premises.
Data Storage and Analytics
- Data Security: VPC isolates your data storage resources like Amazon S3 buckets and relational databases (RDS) within your private network. This protects your data from unauthorized access over the public internet.
- Access Control: You can define granular access controls through security groups and VPC endpoints to restrict access to your data storage only from authorized applications or users within your VPC.
- Data Encryption: VPC integrates with AWS Key Management Service (KMS) to encrypt your data at rest and in transit, adding an extra layer of security for sensitive information.
- Performance Optimization: VPC allows you to place your data analytics services (e.g., Amazon Redshift) in the same VPC as your data storage, minimizing network latency and improving performance for data analytics workloads.
Disaster Recovery
- Redundancy: You can create a secondary VPC in a different AWS region to serve as your disaster recovery (DR) site. This allows you to replicate your critical resources and applications in the DR VPC for failover in case of an outage in the primary region.
- Fast Recovery: By having a pre-configured DR environment within a VPC, you can quickly restore critical services and minimize downtime in the event of a disaster.
- Cost-Effectiveness: You can leverage features like VPC snapshots and Elastic Block Store (EBS) replication to create cost-efficient backups of your resources in the DR VPC, ensuring data protection without incurring unnecessary ongoing costs.
- Testing and Validation: VPC allows you to easily test your DR failover plan by conducting drills and switching traffic to your DR environment without impacting production in the primary region.
- Developing and Testing Environments: Create isolated VPCs for development, testing, and staging environments. This keeps development activities separate from production, preventing accidental changes from impacting critical systems. You can also control access and resource allocation for these environments.
High-Performance Computing (HPC)
- Leverage VPCs to build secure and scalable HPC clusters. Utilize features like private subnets and security groups to restrict access to HPC resources and optimize network traffic flow for high-performance workloads.
Containerized Applications
- Deploy containerized applications (e.g., Docker containers) within a VPC for improved security and isolation. You can leverage VPC endpoints to securely connect your containerized applications to specific AWS services without requiring internet access.
Internet of Things (IoT) Deployments
- Use VPCs to manage and secure IoT devices. Implement private subnets for your IoT devices to isolate them from unauthorized access and control communication between the devices and other resources in your VPC.
Regulatory Compliance:
- VPCs can help you meet specific industry regulations that require data residency or control access to sensitive information. By isolating your resources and implementing access controls, you can demonstrate compliance with regulations like HIPAA or PCI DSS.
Cost Optimization:
- VPC features like network ACLs and VPC endpoints can help you optimize your network costs. By controlling traffic flow and restricting unnecessary internet access, you can reduce egress charges and minimize unnecessary data transfer.
Step-by-Step How-Tos
1. Creating a VPC
- Log in to the AWS Management Console.
- Navigate to the VPC Dashboard.
- Click on "Create VPC".
- Enter the details:
Name tag: Give your VPC a meaningful name.
IPv4 CIDR block: Define the IP range (e.g., 10.0.0.0/16).
IPv6 CIDR block (optional).
Tenancy: Choose between Default or Dedicated. - Click "Create VPC".
2. Configuring Subnets
- In the VPC Dashboard, select **Subnets** and click **Create Subnet**.
- Enter the details:
Name tag: Name your subnet.
VPC: Select the VPC you just created.
Availability Zone: Choose an AZ (or leave it to AWS to select).
IPv4 CIDR block: Define the subnet range (e.g., 10.0.1.0/24). - Click "Create Subnet".
3. Setting Up an Internet Gateway
- In the VPC Dashboard, select "Internet Gateways" and click "Create Internet Gateway".
- Enter a name for the Internet Gateway.
- Click "Create" and then "Attach to VPC".
- Select your VPC from the list and attach the Internet Gateway.
4. Configuring Route Tables
- In the VPC Dashboard, select **Route Tables** and click **Create Route Table**.
- Enter the details:
Name tag: Give your route table a name.
VPC: Select the VPC you created. - Click "Create".
- Select the new route table, go to the "Routes" tab, and click "Edit routes".
- Add a new route:
Destination: `0.0.0.0/0`
Target: Select the Internet Gateway you created. - Click "Save routes".
- Associate the route table with your subnets: Go to the "Subnet Associations" tab, click "Edit subnet associations", and select the subnets to associate.
5. Configuring Security Groups
- In the VPC Dashboard, select **Security Groups** and click **Create Security Group**.
- Enter the details:
Name tag: Name your security group.
Description: Provide a description for the security group.
VPC: Select your VPC.
3. Click "Create".
4. Select the security group, go to the "Inbound rules" tab, and click "Edit inbound rules".
5. Add rules to allow traffic (e.g., HTTP, HTTPS, SSH).
6. Click "Save rules".
6. Configuring Network ACLs
Network Access Control Lists (ACLs) provide an additional layer of security at the subnet level.
- In the VPC Dashboard, select "Network ACLs" and click "Create Network ACL".
- Enter the details:
Name tag: Name your ACL.
VPC: Select your VPC. - Click "Create".
- Select the ACL, go to the "Inbound Rules" tab, and click "Edit Inbound Rules".
- Add rules to allow or deny traffic.
- Repeat for "Outbound Rules" if necessary.
- Go to the "Subnet Associations" tab and associate the ACL with the desired subnets.
Advanced Topics
Peering Connections
VPC peering connections allow you to connect two VPCs, enabling resources in each VPC to communicate with each other as if they were within the same network. This is useful for multi-region deployments or cross-account connectivity.
Create a VPC Peering Connection:
1. In the VPC Dashboard, select Peering Connections and click "Create Peering Connection".
2. Enter the details for the peering connection:
- Name tag: Give your peering connection a name.
- VPC Requester: Select your VPC.
- VPC Accepter: Select the VPC to peer with.
3. Click Create Peering Connection.
4. Accept the peering connection in the accepter VPC.
5. Configure Route Tables to enable communication between VPCs.
VPN and Direct Connect
- VPN: Establish a secure connection between your on-premises network and your AWS VPC.
1. In the VPC Dashboard, select VPN Connections and click Create VPN Connection.
2. Enter the details, including the customer gateway IP.
3. Configure your on-premises VPN device with the provided information.
- Direct Connect: Create a dedicated network connection from your premises to AWS, providing lower latency and higher throughput.
1. In the AWS Management Console, navigate to the Direct Connect dashboard.
2. Click Create Connection and follow the instructions.
Network Address Translation (NAT)
Use a NAT gateway or instance to allow instances in a private subnet to connect to the internet while preventing inbound internet traffic from directly accessing those instances.
1. Create a NAT Gateway:
- In the VPC Dashboard, select "NAT Gateways" and click "Create NAT Gateway".
- Select the subnet and allocate an Elastic IP.
- Click "Create NAT Gateway".
2. Update Route Tables:
- Go to the route table associated with your private subnet.
- Add a route with destination `0.0.0.0/0` and target as the NAT Gateway.
3. VPN Connections: Create secure tunnel connections between your VPC and your on-premises network using industry-standard VPN protocols.
- VPC Endpoints: Allow private connectivity between your VPC and specific AWS services without requiring an internet gateway or NAT instance. This keeps your traffic within the AWS network for increased security and performance.
- Transit Gateway: Acts as a central hub for routing traffic between multiple VPCs and AWS services. It simplifies managing complex network architectures with many VPCs.
Best Practices
1. Planning and Design:
- Define Your Needs: Before creating a VPC, clearly define your application requirements, security needs, and traffic flow. This will help you determine the optimal subnet structure, security group configuration, and routing strategy.
- Start Simple: Begin with a single VPC for basic deployments. As your needs grow, consider using multiple VPCs with specific purposes (e.g., production, development) or a Shared VPC for centralized management across accounts.
- Use Clear Naming Conventions: Implement consistent naming conventions for VPCs, subnets, security groups, and resources for better organization and easier identification.
2. Security Hardening:
- Principle of Least Privilege: Apply the principle of least privilege to security groups and network ACLs. Grant only the necessary traffic flow based on application needs.
- Default Deny: Use a "deny all" approach for inbound traffic in security groups and network ACLs. Explicitly allow only authorized traffic based on source IP, port, and protocol.
- Monitor and Audit: Regularly monitor and audit your VPC configurations for potential security vulnerabilities. Consider using AWS Security Hub and VPC Flow Logs for comprehensive monitoring.
3. Segmentation and Isolation:
- Subnet Strategy: Design your subnet structure based on security requirements and traffic flow. Use separate subnets for public-facing resources (web servers) and private resources (databases) within the same VPC.
- Public vs. Private Subnets: Place resources requiring internet access in public subnets with a route to the internet gateway. Keep sensitive resources in private subnets without internet access, potentially using NAT gateways for controlled outbound communication.
- Security Group Placement: Attach security groups directly to individual instances for granular control over inbound and outbound traffic. Avoid attaching security groups to subnets unless absolutely necessary.
4. Resource Management and Efficiency:
- Utilize VPC Endpoints: Leverage VPC endpoints for secure and private communication between your VPC resources and specific AWS services (e.g., S3, DynamoDB) without internet access. This reduces reliance on internet gateways and potentially lowers egress costs.
- Optimize Resource Allocation: Right-size your VPC resources based on workload demands. Utilize features like Auto Scaling for web servers to automatically scale instances based on traffic patterns.
- Cost Monitoring and Management: Monitor your VPC costs and identify areas for optimization. Consider using AWS Cost Explorer to track resource usage and identify opportunities for cost savings.
5. Maintainability and Automation:
- Use Infrastructure as Code (IaC): Leverage IaC tools like AWS CloudFormation or Terraform to define and automate your VPC configurations. This ensures consistent deployments and simplifies infrastructure management.
- Version Control: Maintain version control for your IaC templates to track changes and easily revert to previous configurations if necessary.
- Test and Validate: Thoroughly test your VPC configurations and security groups before deploying them to production. Use tools like VPC Reachability Analyzer to validate network connectivity.
Final Thoughts
Mastering AWS VPC is crucial for building secure, scalable, and efficient cloud architectures. By understanding the fundamentals, exploring use cases, and following best practices, you can leverage VPCs to meet your organization's networking needs effectively. Whether you’re hosting web applications, extending your on-premises infrastructure, or setting up disaster recovery solutions, AWS VPC provides the tools and flexibility to build robust cloud environments.
Happy Clouding!!!
Did you like this post?
If you did, please buy me coffee 😊