Master AWS Config With A Hands-on Console Walkthrough

AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. It continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations. This helps ensure compliance with internal policies and regulatory standards, making it easier to manage changes and troubleshoot issues.
It provides a detailed view of your resource configurations, including how they are related to each other and how they have changed over time.
AWS Config works by continuously recording the configuration details of your AWS resources. It delivers this information to an Amazon S3 bucket that you specify, where it is stored as configuration history files. These files contain details about the changes made to your resources, including the time of the change, the identity of the user who made the change, and the specific configuration values that were modified.
AWS Config also allows you to define custom configuration rules. These rules can be used to evaluate your resources against your desired configuration settings. If a resource is found to be out of compliance with a rule, AWS Config can send you an alert or take corrective action, such as automatically remediating the issue.
AWS Config can be very usefule for Security and Compliance Audits, Change Management, Operational Troubleshooting and Resource Inventory.
I have previously written an article about AWS Config and you can find it here. I stronly recommend readig the article first before going through this hands-on exercise.
There are three major steps involved in setting up AWS Config:
Set Up AWS Config
Create AWS Config Rules
Monitor and Manage Compliance
Step 1: Set up AWS Config
Visit the AWS Config console and click on get started.
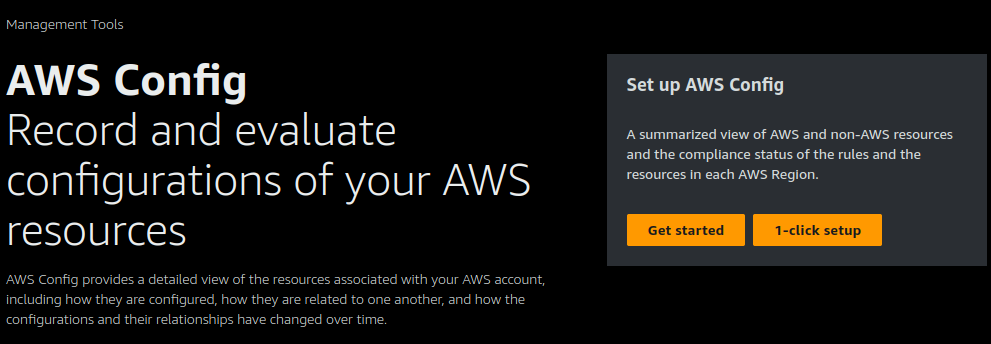
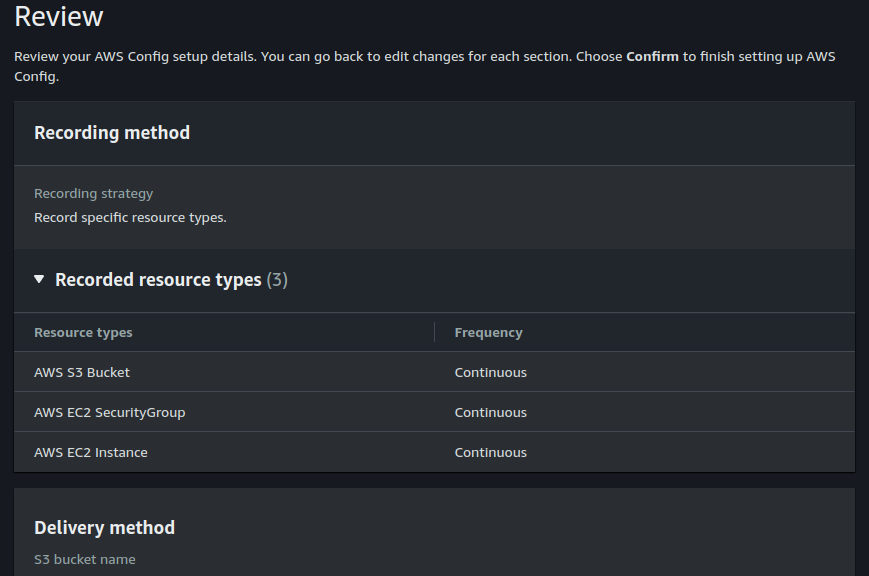
The first thing we'll do here is to select the resources we want to record. You can choose to record all resource types or select specific resources to record.
You can also choose the frequency with which AWS Config will record your resources. I am choosing to monitor my S3 buckets, EC2 sceurity groups and EC2 instances.
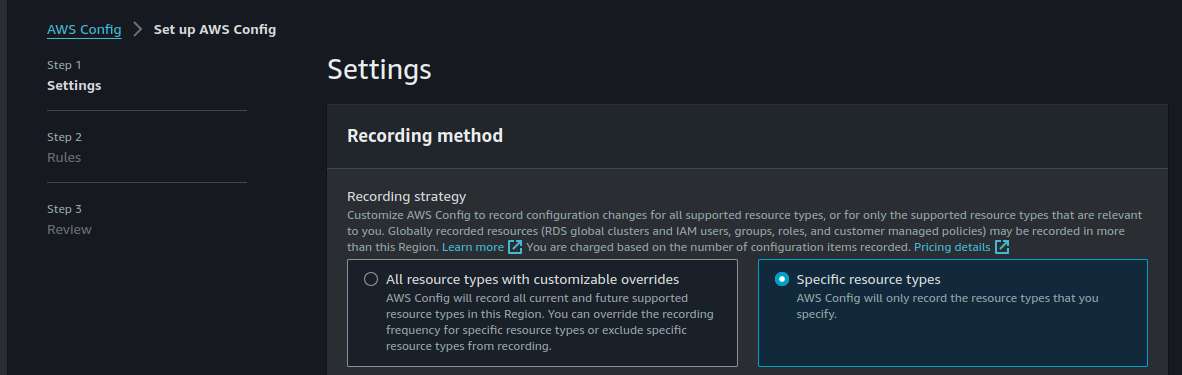
For the purposes of this excercise, I will choose to monitor my selected resources continuously.
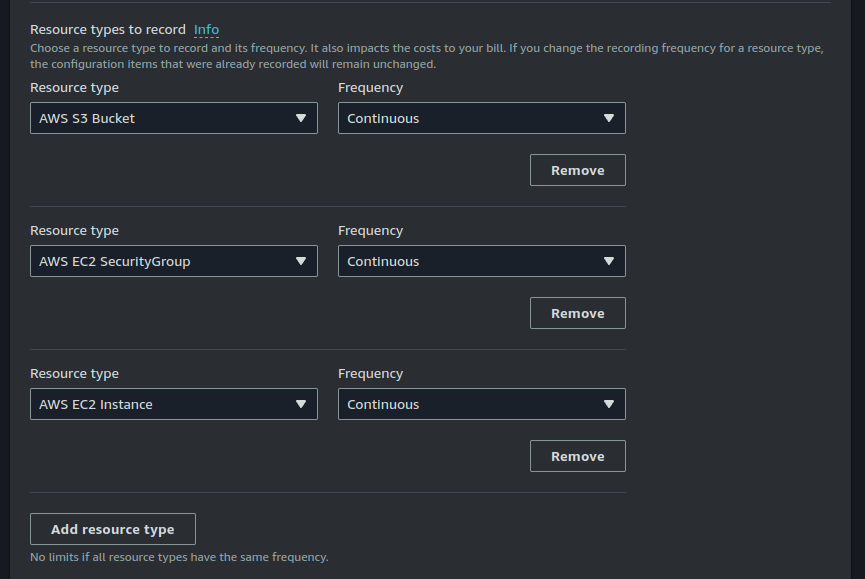
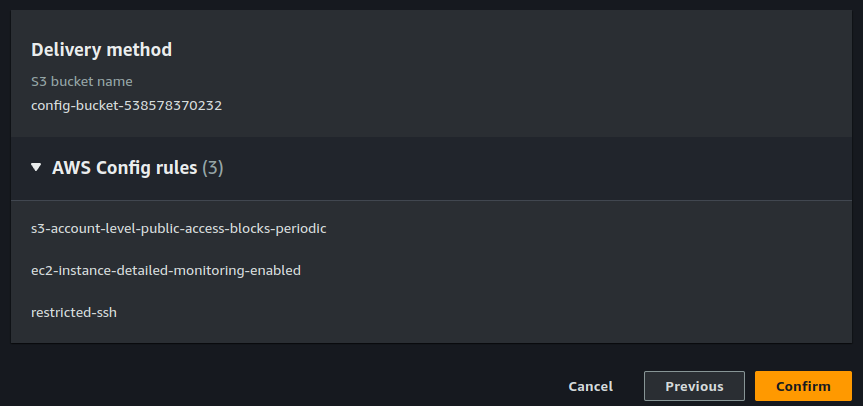
Create a role for Config and select a destination S3 bucket where configuration record will be stored.
You can also choose to enable SNS notifications for configuration changes. I will not be doing that here.
Click on Next.
Select rules for EC2 detailed monitoring, S3 public access and security group restricted ssh.
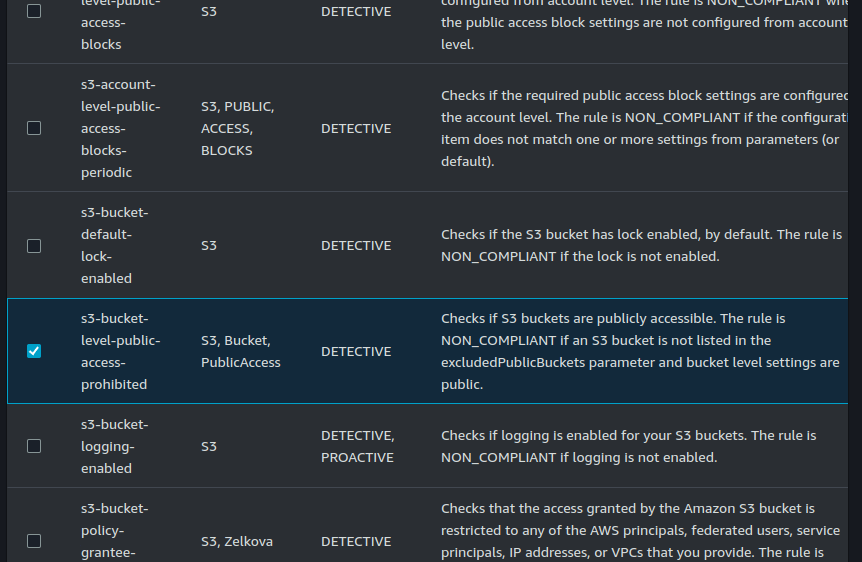
Go to the review page.
Let us now walk through the console to better understand the different aspects of AWS Config.
- AWS Config Dashboard: This is the monitoring console which provides a broad overview of your conifgurations, conformance packs, compliance status and usage metrics.
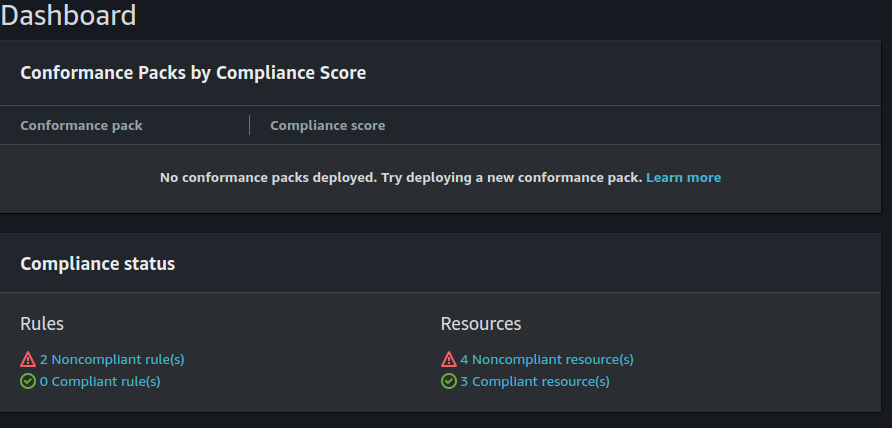
You can see here that I have two non-compliant rules and four non-compliant resources.
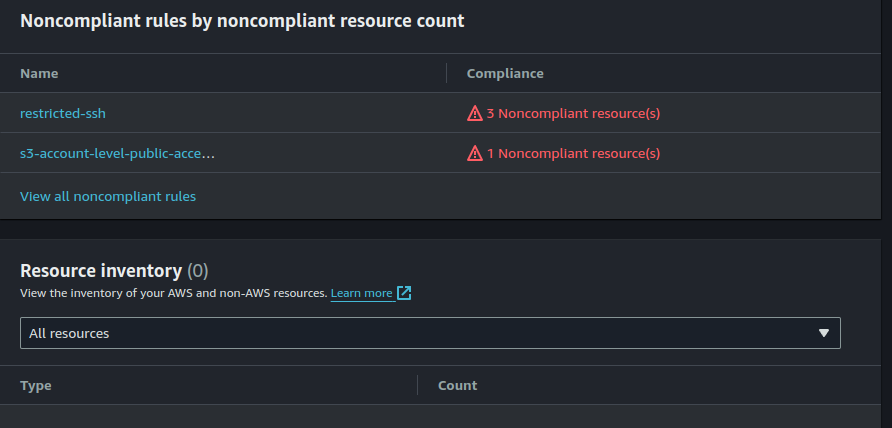
The bottom of the dashboard provides usage metrics and success metrics.
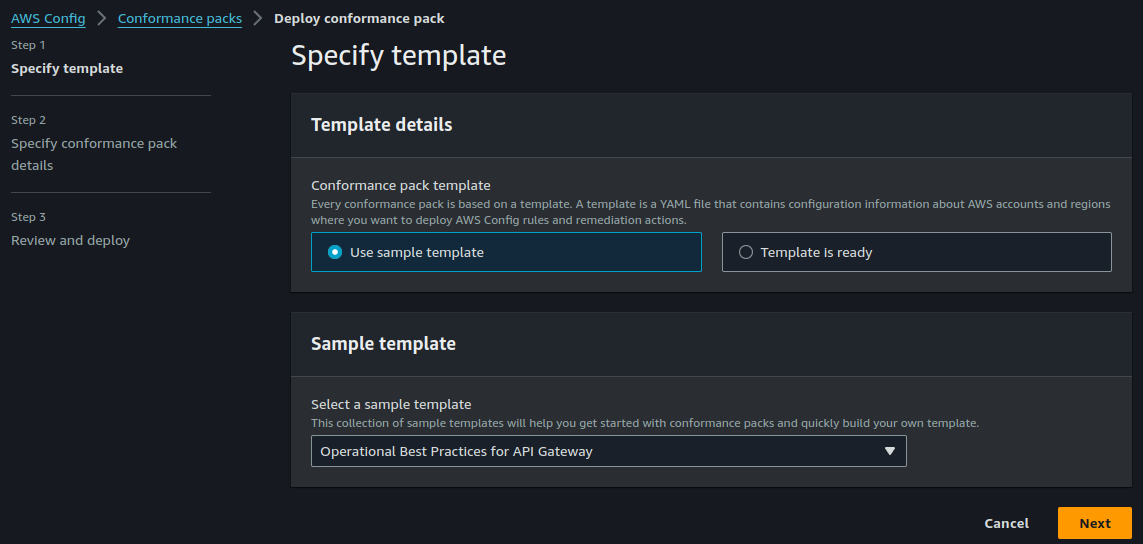
- AWS Config Conformance packs: Here is an explanation about Conformance packs; Conformance Packs bundle pre-defined AWS Config rules. These rules act as guidelines for your cloud resources, dictating security best practices, resource optimization strategies, and adherence to internal policies. Conformance Packs allow you to deploy a collection of rules across your entire AWS environment in a single action, saving you time and effort. They also provide a unified view of your configuration state, making it easy to identify and address any deviations from your desired standards. Finally, they can be configured to provide automatic remediation when necessary. You can find sample conformance packs here on GitHub.
- You can choose from a variety of pre-built templates or even create your own.
- AWS Config rules:
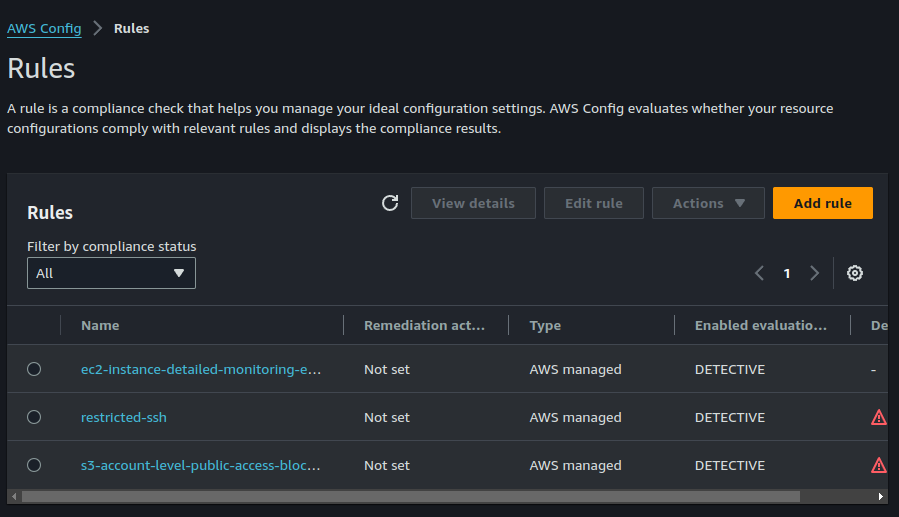
AWS Config rules are the building blocks for ensuring your cloud resources are configured securely and follow best practices. They act like automated inspectors, constantly evaluating your AWS resources against a set of criteria you define. There are two main types of AWS Config rules: AWS Managed rules and AWS Custom rules. AWS Managed rules are pre-built rules developed by AWS itself. They cover a wide range of areas, like security best practices, cost optimization, and service-specific configurations. You can simply activate these rules and they'll start evaluating your resources. That is just what we have done here. AWS custom rules on the other hand are used when you have specific needs that are not addressed by managed rules. You can do this by creating them within your AWS Lambda functions.
AWS Config Resource Inventory: AWS Config resource inventory is a continuously updated catalog of all your AWS resources. It includes details like resource type, configuration settings, and tags. This inventory provides a central view of your cloud environment, enabling you to track resource usage, identify configuration drift, and ensure compliance.
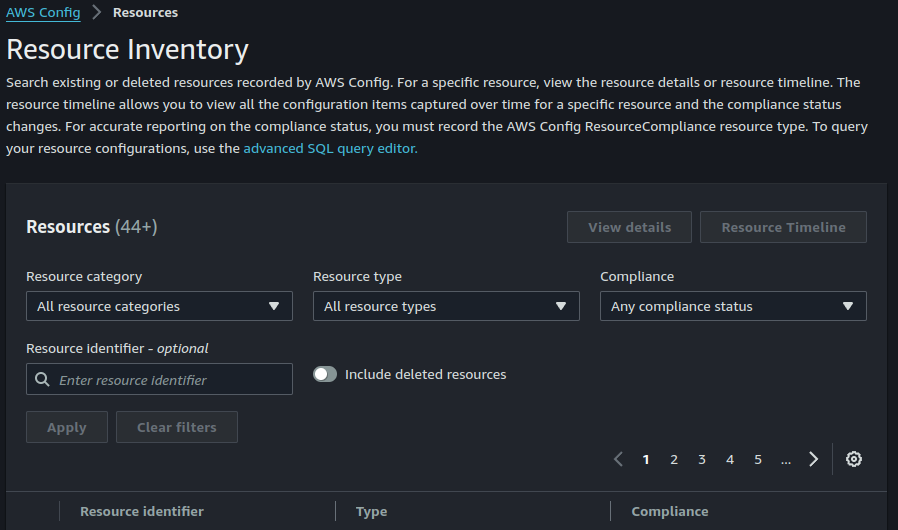
AWS Config Aggregators: Here's a good explanation of AWS Config aggregators; AWS Config aggregators act like central hubs for configuration data. They allow you to consolidate AWS Config information from:
- Multiple Accounts: Instead of managing compliance and configurations individually in each account, an aggregator brings data from various accounts into a single location for centralized monitoring.
- Multiple Regions: Data from different regions within an account can also be aggregated, providing a unified view of your entire cloud footprint.
- AWS Organizations: If you use AWS Organizations, an aggregator can collect data from all member accounts that have AWS Config enabled.
This consolidated view empowers you to:
- Simplify Compliance Monitoring: Easily assess the configuration state and compliance posture across your entire AWS environment.
- Reduce Management Overhead: Manage configurations and rules from a single location, saving time and effort.
- Gain Centralized Insights: Analyze configuration data from all sources to identify trends, potential risks, and opportunities for improvement.
Think of it as organizing scattered puzzle pieces (configuration data) from different boxes (accounts and regions) into a complete picture (centralized view) for better understanding and control.
Step 2: Implement remediation actions
Now that we have gone through most of the AWS Config console, let us talk about AWS Config remediation actions.
AWS Config remediation actions are automated steps you can configure to address resources that violate your defined rules. They essentially act like a "fix-it" button for non-compliant configurations.
There are two main types of remediation actions:
- Manual Remediation: When a rule violation occurs, AWS Config notifies you. You can then manually review the issue and take corrective action through the AWS Management Console or the AWS CLI.
- Automatic Remediation (Optional): This powerful feature allows you to pre-define actions that AWS Config will automatically execute when a resource violates a rule. These actions can involve:
- Sending Notifications: Alerting designated personnel via email or SNS about the non-compliant resource.
- Logging Events: Recording details of the violation in CloudWatch logs for further analysis.
- Taking Corrective Actions: In some cases, AWS Config can automatically fix the configuration issue itself. This might involve stopping an EC2 instance without encryption or enabling deletion protection for an S3 bucket.
Benefits of Remediation Actions:
- Faster Resolution: Automatic actions can resolve compliance issues swiftly, minimizing the risk window.
- Reduced Manual Work: Free yourself from manually fixing configuration errors, allowing you to focus on other tasks.
- Improved Consistency: Automated remediation ensures consistent enforcement of your compliance policies.
Important Considerations:
- Not all rules support automatic remediation.
- You need to configure the specific actions you want AWS Config to take.
- Ensure the IAM role used for remediation has the necessary permissions to perform the actions.
By leveraging remediation actions, you can transform your AWS Config rules from simply identifying issues to actively resolving them, creating a more proactive and automated approach to cloud compliance.
Select the ssh-restricted rule. click on Actions > Manage remediation.
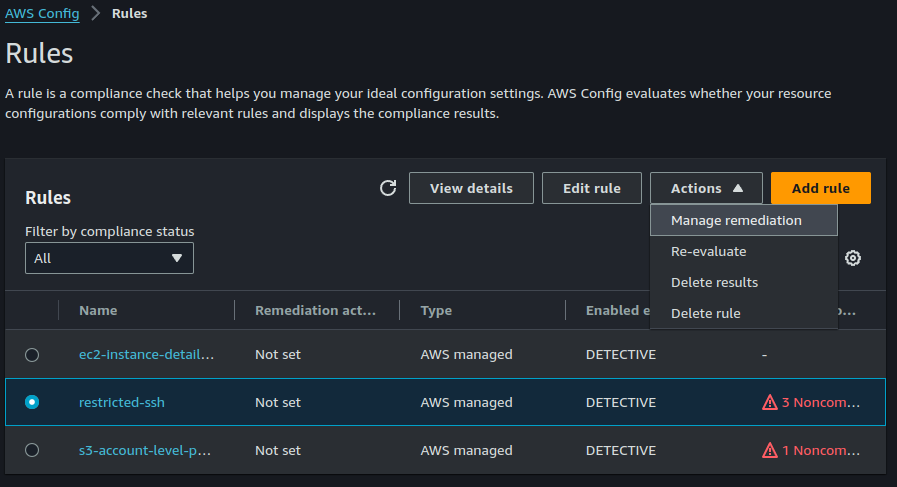
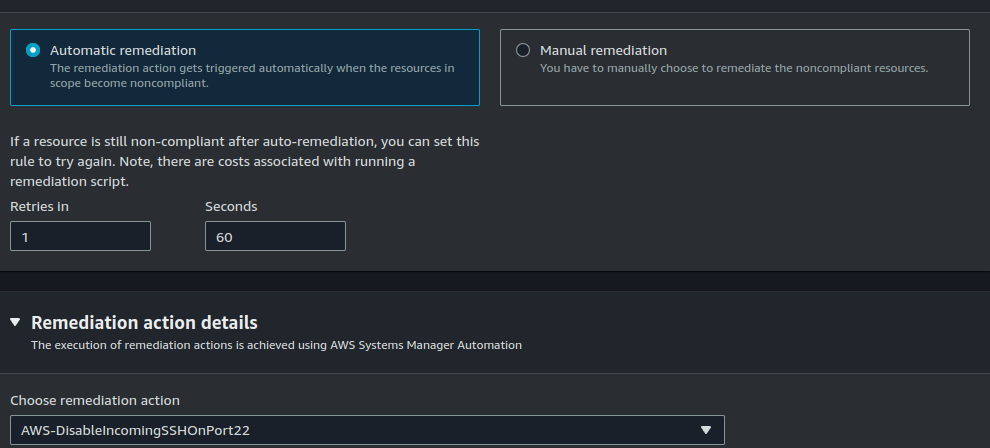
You can choose between automatic and manual remediation based on what's best for you. I am selecting automatic remediation. I also chose to retry the remediation action once per minute if resource is still non compliant.
Final Thoughts
This is just a starting point. As you gain experience, you can explore pre-built managed rules, compliance packs, and aggregators to further strengthen your cloud security posture.
Remember, AWS Config is a valuable tool for managing and securing your AWS environment. By implementing it effectively, you can achieve a more compliant, secure, and cost-optimized cloud infrastructure.
Happy Clouding !!!
Did you like this post?
If you did, please buy me coffee 😊