From Concept to Deployment: A Practical Guide to Implementing Serverless Networking with AWS Lambda@Edge

Serverless computing has revolutionized the way developers deploy and manage applications by abstracting the underlying infrastructure. AWS Lambda@Edge takes this innovation further by allowing you to run code closer to your users, reducing latency and improving performance. In this comprehensive, hands-on guide, we'll take you from concept to deployment, demonstrating how to implement serverless networking using AWS Lambda@Edge. You'll learn the technical aspects, explore scenarios and use cases, and follow detailed steps to build and deploy your own serverless applications.
What is AWS Lambda@Edge?
AWS Lambda@Edge is a feature of Amazon CloudFront - the Content Delivery Network (CDN) service by AWS - that lets you run serverless functions at AWS edge locations worldwide. This enables you to execute code in response to events generated by CloudFront, such as viewer requests and origin responses, thereby boosting the performance and scalability of your applications.
Key Features
- Global Execution: Run code at AWS edge locations worldwide, minimizing latency.
- Scalability: Automatically scale your functions without managing servers.
- Security: Integrate with AWS Identity and Access Management (IAM) for fine-grained access control.
- Flexibility: Trigger functions based on CloudFront events like viewer requests, origin responses, and more.
AWS Lambda@Edge vs. CloudFront Functions
Before diving into Lambda@Edge, it's important to understand how it compares with CloudFront Functions, another feature of Amazon CloudFront. Here's a side-by-side comparison to highlight the key differences:
| Feature | AWS Lambda@Edge | CloudFront Functions |
|---|---|---|
| Execution Location | Edge locations (globally) | Edge locations (globally) |
| Use Cases | Complex processing, HTTP responses | Lightweight processing, HTTP equest/response manipulation |
| Supported Languages | Node.js, Python, others | JavaScript |
| Execution Time Limit | 5 seconds | 1 millisecond |
| Resource Limits | 128 MB memory, 50 MB package size | 2 MB memory, 1MB package size |
| Invocation Cost | Higher (due to more complex functions) | Lower (optimized for lightweight processing) |
| IAM Integration | Fulll IAM integration | Simolified permissions |
When to Use Each
- AWS Lambda@Edge: Best suited for complex tasks that require more processing power and time, such as dynamic content generation, complex request/response transformations, and heavy computations.
- CloudFront Functions: Ideal for lightweight operations with minimal latency, such as simple header manipulations, redirects, and A/B testing.
Technical Details of Lambda@Edge
Architecture
Lambda@Edge functions are deployed globally across AWS edge locations. The architecture involves:
- CloudFront Distribution: Distributes your content across edge locations.
- Lambda@Edge Functions: Triggered by CloudFront events.
- AWS Edge Locations: Points of presence where your code executes.
Event Types
Lambda@Edge supports several CloudFront event types:
- Viewer Request: Triggered when a request is received from the end user.
- Viewer Response: Triggered before returning the response to the end user.
- Origin Request: Triggered before forwarding the request to the origin server.
- Origin Response: Triggered when a response is received from the origin server.
Permissions
Lambda@Edge uses IAM roles to manage permissions. You need to create an IAM role with the necessary policies to allow Lambda to assume the role and access required resources.
Scenarios and Use Cases
Dynamic Content Generation
Lambda@Edge can be used to generate dynamic content at the edge, such as personalizing web pages based on user attributes.
Example: A news website can personalize headlines based on the user's location or preferences.
Security and Authentication
Enhance security by implementing custom authentication and authorization logic at the edge.
Example: Block malicious IP addresses or add custom headers to requests for security purposes.
SEO Optimization
Modify HTTP headers and status codes to improve SEO.
Example: Redirect HTTP requests to HTTPS or implement URL rewrites for better search engine indexing.
A/B Testing
Run A/B tests by modifying responses at the edge without impacting the origin server.
Example: Serve different versions of a webpage to different users to test which performs better.
How-to Guide: Implementing Lambda@Edge
Scenario 1: Implement SEO Optimization For A Static Website by Redirecting HTTP Requests to HTTPS
Step 1: Create and Configure your S3 Bucket
1. Navigate to the S3 Console and click on "Create Bucket"
2. Select the bucket. Go to "Permissions" > "Bucket policy" > "Edit Policy". Add the followin permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Principal": "*",
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": ["YOUR-S3-BUCKET-ARN/*"]
}
]
}Now that we have create the bucket, we must upload the static (HTML/CSS) Code.
Create a file named "index.html" with the HTML code below and upload into your bucket.
<html>
<head>
<title>My Static Website</title>
</head>
<body>
<h1>Hello world</h1>
<h2>This is a static website, distributed by CloudFront</h1>
</body>
</html>
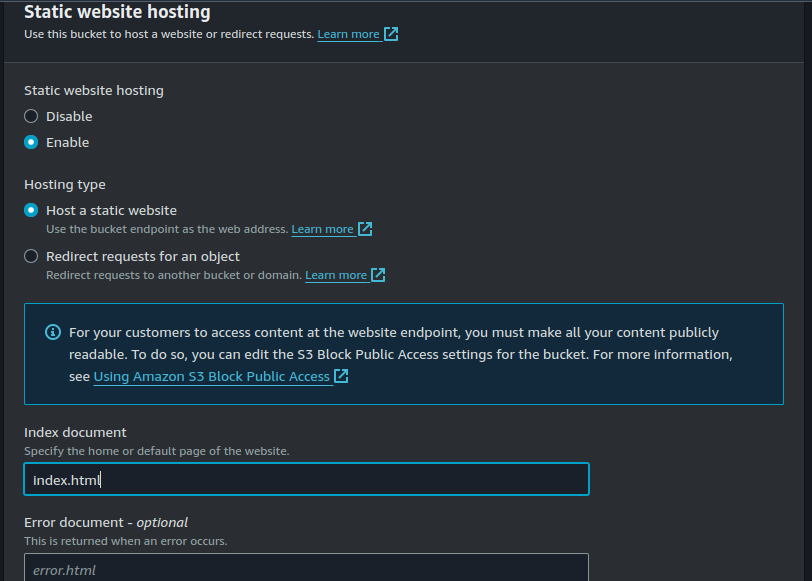
Go to your s3 bucket. Click on "Properties" >"Static website hosting"> "Enable".
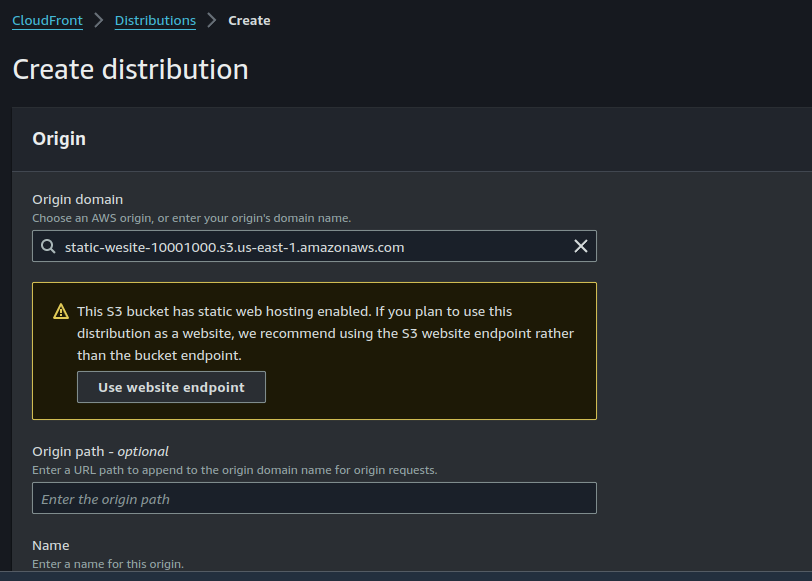
Step 2: Create a cloudFront Distribution
In the CloudFront console, click on "Create Distribution".
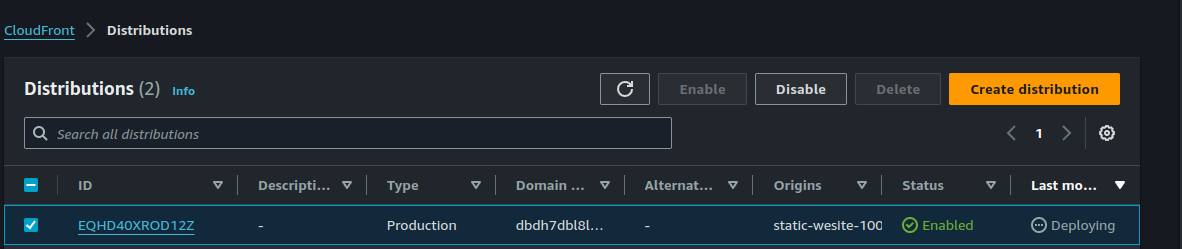
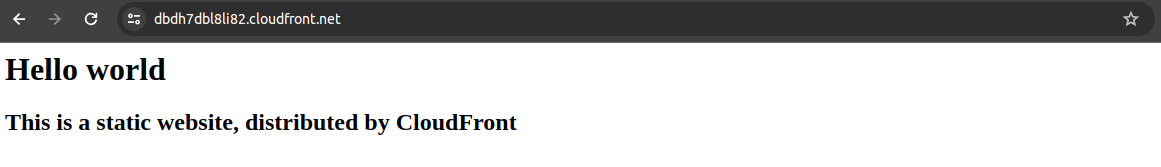
Copy the distribution domain name and paste in a web browser, you should be able to view the web content.
Step 3: Create a Lambda Function
1. Navigate to AWS Lambda Console.
2. Create Function: Choose "Blueprint"
3. Choose "Create from scartch"
4. Function Name: Provide a meaningful name.
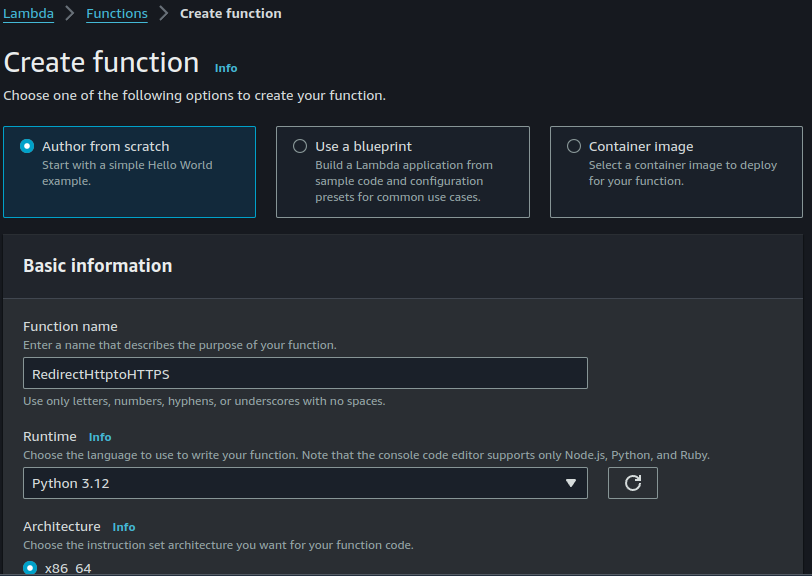
5. Permissions: Create a new role with basic Lambda permissions.
Step 4: Write Your Function Code
Example of a simple function to redirect HTTP to HTTPS:
def handler(event, context):
request = event['Records'][0]['cf']['request']
headers = request['headers']
if headers['x-forwarded-proto'][0]['value'] != 'https':
return {
'status': '301',
'statusDescription': 'Moved Permanently',
'headers': {
'location': [{
'key': 'Location',
'value': f"https://{headers['host'][0]['value']}{request['uri']}"
}]
}
}
return request
Click on "Deploy".
Step 5: Modify the lambda IAM execution role
- Go to the IAM console and navigate to the role used as the execution role for the Lambda function
- Click on the "Trust relationships" tab and click "Edit trust relationship"
- In the "Principal" section, add the following JSON object:
{ "Service": "edgelambda.amazonaws.com" }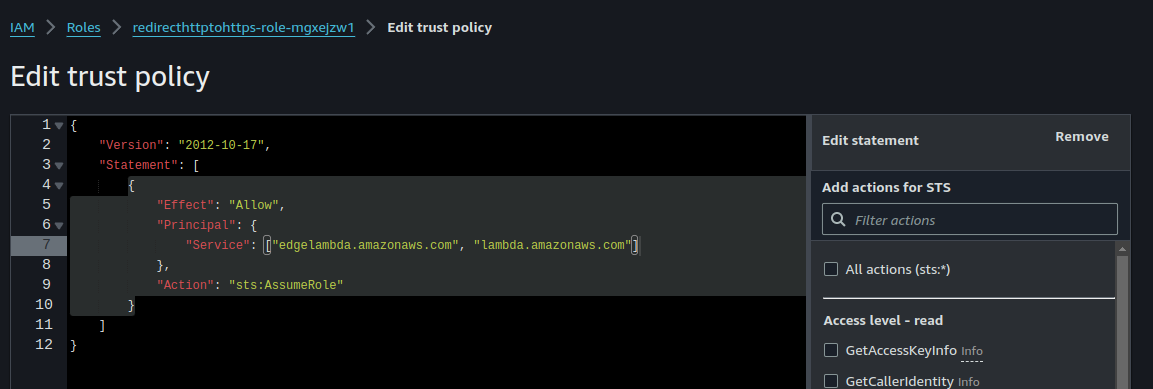
4. Click "Update Trust Policy" to save the changes
This will allow the "edgelambda.amazonaws.com" service principal to assume the role.
Step 6: Deploy the Lambda Function
1. Deploy to Lambda@Edge: Navigate to the Lambda function and choose "Actions" > "Deploy to Lambda@Edge."
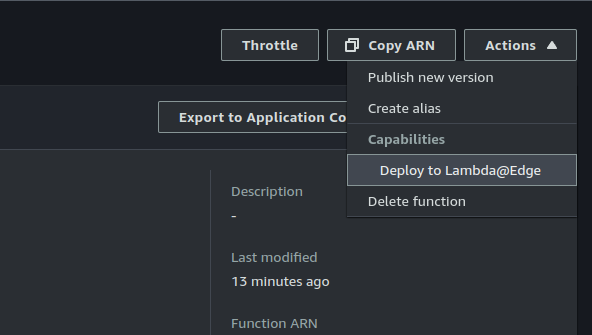
2. CloudFront Association: Select the CloudFront distribution and the event type (Viewer Request).
3. Replication: AWS replicates the function across edge locations.
Step 7: Update CloudFront Distribution
1. Navigate to CloudFront Console.
2. Select Distribution: Choose the CloudFront distribution you want to update.
3. Behavior: Update the behavior settings to associate the Lambda function with the relevant event.
Click on "Save changes".
Step 5: Test and Monitor
1. Test: Make requests to your CloudFront distribution URL to ensure the Lambda function works as expected.
2. Monitor: Use AWS CloudWatch to monitor the logs and performance of your Lambda@Edge functions.
Best Practices for Implementing AWS Lambda@Edge
Optimize Function Performance
- Minimize Latency: Keep your code efficient to minimize execution time.
- Reduce Payload Size: Use compact data formats for request and response payloads.
Security
- IAM Policies: Use least privilege principles for IAM roles.
- Environment Variables: Store sensitive information securely using environment variables.
Testing
- Local Testing: Use AWS SAM (Serverless Application Model) for local testing.
- Edge Testing: Test your functions in different geographical locations to ensure consistent performance.
Monitoring and Logging
- CloudWatch: Set up CloudWatch alarms and dashboards to monitor function metrics.
- Logging: Ensure that your Lambda function logs necessary information for debugging and monitoring.
FAQs on Lambda@Edge
1. What are the limitations of Lambda@Edge?
- Execution time is limited to 5 seconds.
- Maximum function package size is 50 MB.
- Environment variables and layers are not supported.
2. How does Lambda@Edge differ from AWS Lambda?
- Lambda@Edge functions are deployed globally across edge locations.
- Lambda@Edge is specifically designed to work with CloudFront distributions.
3. Can I use Lambda@Edge for real-time data processing?
- Yes, but keep in mind the execution time limit. It's suitable for mid-weight, low-latency processing.
Final Thoughts
AWS Lambda@Edge provides a powerful platform for implementing serverless networking solutions, bringing computation closer to the user for reduced latency and improved performance. By leveraging its global infrastructure, flexible event triggers, and seamless integration with other AWS services, Lambda@Edge enables developers to build robust, scalable, and secure applications. Whether for dynamic content generation, enhancing security, SEO optimization, or running A/B tests, Lambda@Edge is a versatile tool that can significantly enhance your cloud architecture.
By following this detailed how-to guide and adhering to best practices, you can harness the full potential of Lambda@Edge to deliver high-performance serverless applications.
Happy Clouding!!!
Did you like this post?
If you did, please buy me coffee 😊