A Comprehensive Guide to AWS Config: Monitoring and Compliance Made Easy

In today's dynamic cloud environments, managing and monitoring resources efficiently is critical. AWS Config is a powerful tool that helps organizations achieve this by providing detailed insights into the configuration of their AWS resources. This article delves into AWS Config, exploring its features, benefits, use cases, and how to implement it effectively. Whether you're a cloud architect, systems administrator, or DevOps engineer, understanding AWS Config can significantly enhance your cloud management capabilities.
What is AWS Config?
AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources. It continuously monitors and records your AWS resource configurations and allows you to automate the evaluation of recorded configurations against desired configurations. This helps ensure compliance with internal policies and regulatory standards, making it easier to manage changes and troubleshoot issues.
It provides a detailed view of your resource configurations, including how they are related to each other and how they have changed over time.
How It Works
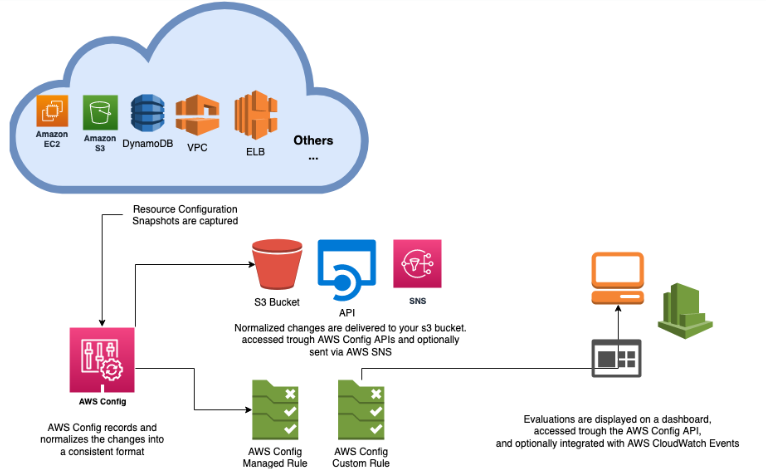
AWS Config works by continuously recording the configuration details of your AWS resources. It delivers this information to an Amazon S3 bucket that you specify, where it is stored as configuration history files. These files contain details about the changes made to your resources, including the time of the change, the identity of the user who made the change, and the specific configuration values that were modified.
AWS Config also allows you to define custom configuration rules. These rules can be used to evaluate your resources against your desired configuration settings. If a resource is found to be out of compliance with a rule, AWS Config can send you an alert or take corrective action, such as automatically remediating the issue.
Key Features of AWS Config
- Continuous Monitoring: AWS Config continuously monitors and records your AWS resource configurations. This means that any change in configuration is tracked, providing a comprehensive history of changes over time. This historical data is invaluable for auditing and troubleshooting purposes.
- Configuration Snapshot and History: AWS Config provides a snapshot of the current configuration of your AWS resources. It also maintains a history of configuration changes, which can be used to understand how a resource’s configuration has evolved over time. This is crucial for compliance audits and for understanding the state of your resources at any point in time.
- Configuration Rules: AWS Config allows you to define rules that represent your ideal resource configurations. These rules automatically check the configuration of your resources and provide compliance statuses. AWS provides a set of managed rules, and you can also create custom rules using AWS Lambda.
- Integration with AWS Services: AWS Config integrates seamlessly with other AWS services like AWS CloudTrail, AWS Lambda, Amazon CloudWatch, and AWS Systems Manager. This integration allows you to automate responses to non-compliant configurations, trigger notifications, and take remedial actions.
Benefits of Using AWS Config
- Enhanced Visibility: AWS Config provides detailed visibility into the configuration of your AWS resources. This visibility is essential for understanding the state of your infrastructure and ensuring that it meets your operational and security requirements.
- Improved Compliance: By using AWS Config rules, you can automatically check the compliance of your resource configurations against internal policies and external regulations. This helps in maintaining compliance and avoiding potential penalties.
- Simplified Auditing: The historical data provided by AWS Config simplifies the auditing process. Auditors can easily access configuration histories and change details, making it easier to verify compliance and investigate issues.
- Efficient Troubleshooting: When configuration issues arise, AWS Config’s detailed records and historical data make troubleshooting more efficient. You can quickly identify when and how a resource’s configuration was changed, which helps in pinpointing the root cause of issues.
Use Cases for AWS Config
- Security and Compliance Audits: Organizations can use AWS Config to ensure their resources comply with security policies and regulatory requirements. For example, AWS Config can check whether S3 buckets are publicly accessible, whether IAM roles adhere to least privilege principles, and whether encryption is enabled for sensitive data.
- Change Management: AWS Config helps manage changes to your infrastructure by providing a detailed history of configuration changes. This is particularly useful in environments where changes are frequent, as it helps in tracking changes and understanding their impact.
- Operational Troubleshooting: When operational issues occur, AWS Config’s detailed records can help troubleshoot problems more effectively. For instance, if an application suddenly stops working, you can use AWS Config to check if any recent configuration changes might have caused the issue.
- Resource Inventory: AWS Config provides a comprehensive inventory of your AWS resources and their configurations. This inventory is valuable for understanding your infrastructure, planning resource usage, and optimizing costs.
How to Implement AWS Config
Step 1: Set Up AWS Config
1. Sign in to the AWS Management Console and open the AWS Config console.
2. Choose "Get started" if you are using AWS Config for the first time.
3. Specify resource types to record. You can choose to record all resource types or specific ones.
4. Set up Amazon S3 bucket to store configuration history and snapshots. AWS Config will deliver configuration snapshots and history files to this bucket.
5. Set up Amazon SNS topic to receive notifications about configuration changes and compliance events.
6. Review and confirm your settings to start recording configurations.
Step 2: Create AWS Config Rules
1. Navigate to the Rules section in the AWS Config console.
2. Choose "Add rule" to create a new rule.
3. Select a managed rule from the list or define a custom rule using AWS Lambda.
4. Configure rule parameters, such as resource type, compliance criteria, and remediation actions.
5. Review and activate the rule to start evaluating resource configurations against the rule.
Step 3: Monitor and Manage Compliance
1. View compliance status in the AWS Config console to see which resources are compliant or non-compliant with your rules.
2. Investigate non-compliant resources by reviewing the configuration history and change details.
3. Take remediation actions to correct non-compliant configurations. This can be automated using AWS Lambda functions triggered by compliance events.
Step 4: Analyze Configuration Changes
1. Use the timeline view in the AWS Config console to analyze changes to a resource’s configuration over time.
2. Compare configurations to understand differences between current and previous states.
3. Generate configuration snapshots for comprehensive reports on the state of your resources.
Example Scenarios
Scenario 1: Ensuring S3 Bucket Compliance
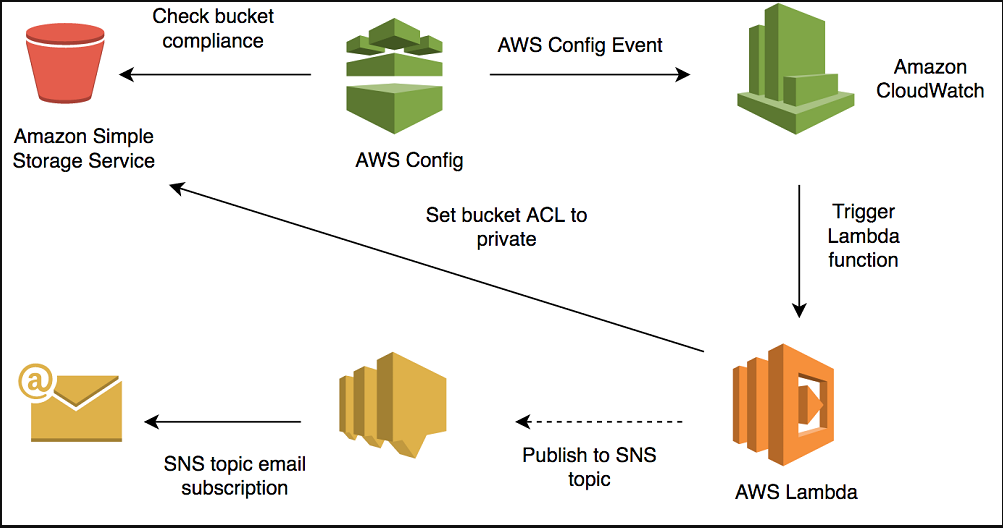
A company needs to ensure that all S3 buckets are not publicly accessible to comply with data privacy regulations. They set up an AWS Config rule to check the accessibility of S3 buckets.
1. Create a managed rule named s3-bucket-public-read-prohibited.
2. Configure the rule to evaluate all S3 buckets in the account.
3. Set up notifications to alert the security team when a bucket is found to be publicly accessible.
4. Remediate non-compliant buckets by automatically triggering an AWS Lambda function to update the bucket policy.
Scenario 2: Monitoring IAM Role Compliance
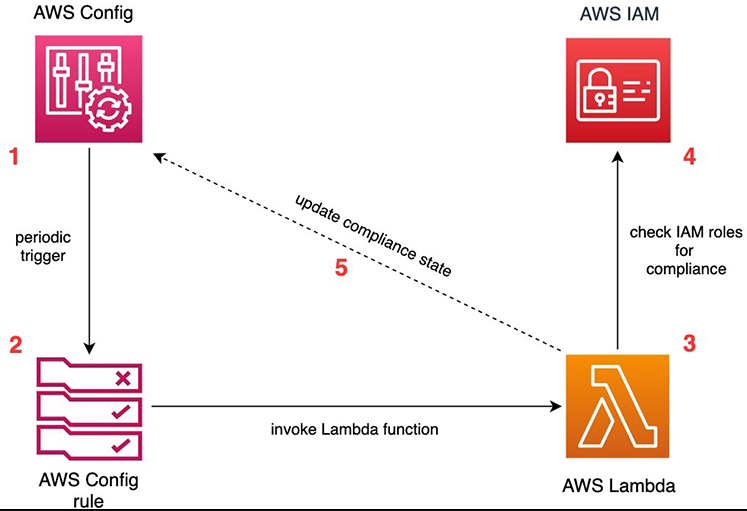
An organization wants to ensure that IAM roles adhere to the principle of least privilege. They define custom AWS Config rules using AWS Lambda to evaluate IAM roles.
1. Create a custom rule using AWS Lambda to check IAM role permissions.
2. Write a Lambda function that evaluates whether the permissions granted are excessive.
3. Deploy the rule and monitor IAM roles for compliance.
4. Receive notifications and investigate any non-compliant roles.
Scenario 3: Auditing EC2 Instance Configurations
A business needs to audit the configurations of their EC2 instances to ensure they meet the required specifications.
1. Set up AWS Config to record configurations for EC2 instances.
2. Define rules to check for compliance with specifications such as instance type, security groups, and tagging.
3. Generate reports using AWS Config snapshots to provide to auditors.
4. Use historical data to investigate any discrepancies found during the audit.
Advanced Concepts and Best Practices
- Automating Remediation Actions: While AWS Config can alert you to non-compliant configurations, automating remediation can save time and reduce human error. Use AWS Lambda functions triggered by AWS Config compliance events to automatically correct non-compliant configurations. For example, if an S3 bucket is found to be publicly accessible, a Lambda function can update the bucket policy to make it private.
- Custom Configuration Rules: For unique compliance requirements, you can create custom AWS Config rules using AWS Lambda. Custom rules can be written in Python or Node.js and allow you to define more granular checks. This is particularly useful for industry-specific compliance standards that are not covered by AWS managed rules.
- Cross-Account Monitoring: In multi-account AWS environments, managing compliance and configuration consistency across all accounts is crucial. AWS Config Aggregator allows you to collect and view configuration and compliance data from multiple accounts and regions in a single account. This centralized view simplifies management and ensures that all accounts adhere to your organization’s standards.
- Leverage AWS Config for Cost Optimization: AWS Config can also be used for cost optimization by identifying unused or underutilized resources. By setting up rules to check for idle EC2 instances, unused EBS volumes, or unattached Elastic IPs, you can receive alerts and take action to shut down or decommission these resources, thereby reducing unnecessary costs.
- Integration with AWS Security Hub: Integrating AWS Config with AWS Security Hub provides a comprehensive view of your security posture. AWS Security Hub aggregates and prioritizes security findings from various AWS services, including AWS Config. This integration allows you to correlate compliance data from AWS Config with other security findings, enabling more effective threat detection and response.
Conclusion
AWS Config is an essential tool for managing and monitoring AWS resource configurations. By providing continuous monitoring, detailed configuration history, and compliance checking, it enhances visibility, simplifies auditing, and improves operational efficiency. Implementing AWS Config involves setting up the service, defining rules, and leveraging its powerful features to maintain compliance and troubleshoot issues effectively. Whether ensuring security compliance, managing changes, or auditing configurations, AWS Config is a valuable asset for any organization leveraging AWS.
By integrating AWS Config into your cloud management strategy, you can achieve a higher level of control and confidence in your AWS environment. Start using AWS Config today to take your cloud resource management to the next level.
Visit the lab to gain a practical experience working with AWS Config.
Happy Clouding !!!
Did you like this post?
If you did, please buy me coffee 😊