A Comprehensive Guide to Amazon GuardDuty: Securing AWS Environments with Advanced Threat Detection

Introduction
As organizations increasingly migrate to the cloud, the security of cloud resources becomes a critical concern. AWS offers a range of security services to protect cloud environments, and Amazon GuardDuty stands out as one of the key players. GuardDuty is a fully managed threat detection service that continuously monitors AWS accounts and workloads for malicious or unauthorized behavior. It leverages machine learning, anomaly detection, and threat intelligence to safeguard cloud environments from evolving threats like compromised accounts, cryptocurrency mining, data exfiltration, and more.
In this detailed guide, we will explore the ins and outs of Amazon GuardDuty, focusing on its features, multi-account strategy, integrations with other AWS services, architectural patterns, and real-world use cases. Whether you're a security professional or a cloud engineer, understanding GuardDuty is crucial to building a robust cloud security framework.
What is Amazon GuardDuty?
Amazon GuardDuty is an advanced, fully managed threat detection service that continuously monitors your AWS accounts, applications, data, and network traffic for suspicious behavior or unauthorized activity. By analyzing logs from various sources, such as VPC Flow Logs, AWS CloudTrail event logs, and DNS query logs, GuardDuty identifies and alerts on a wide range of security issues, from known attack patterns to subtle anomalies.
Key Features of GuardDuty:
- Continuous Monitoring and Threat Detection: GuardDuty operates continuously, analyzing data streams from key AWS services to detect threats in real-time. It inspects incoming and outgoing traffic, API calls, and DNS requests to identify unusual behaviors.
- S3 Protection: GuardDuty extends its protection to Amazon S3, where it monitors for unauthorized access, unusual data downloads, and activities such as brute-force attempts or exfiltration of sensitive data.
- Anomaly Detection with Machine Learning: By leveraging machine learning algorithms, GuardDuty builds a baseline of "normal" activity for each AWS environment and flags any deviations from this baseline as potential threats. This allows it to detect previously unknown threats.
- Threat Intelligence: GuardDuty uses threat intelligence feeds from AWS, third-party providers, and community sources to identify known bad actors, IP addresses, and domains associated with malicious activities like botnets, cryptocurrency mining, and phishing.
- Cost-Effective and Scalable: GuardDuty is a cost-effective solution that requires no upfront infrastructure costs. You are charged based on the volume of data processed, making it scalable as your cloud environment grows.
- Ease of Deployment: GuardDuty requires no software or agent installation. It can be enabled with a few clicks in the AWS Management Console and automatically begins monitoring your environment without requiring any configuration changes to your resources.
Detailed Multi-Account Strategy for GuardDuty
In modern enterprises, it’s common to manage multiple AWS accounts, either for different teams, departments, or environments (development, production, etc.). GuardDuty’s multi-account strategy allows centralized security monitoring across all these accounts, simplifying security management while providing comprehensive threat detection.
1. Centralized Threat Detection with AWS Organizations
AWS Organizations enables you to manage multiple AWS accounts under one organization. With GuardDuty, you can designate a Master (Admin) account that consolidates threat findings from Member accounts within the organization. The Admin account aggregates GuardDuty findings from all linked Member accounts, offering centralized visibility and management.
Steps to Implement a Multi-Account Strategy:
- Enable GuardDuty in the Admin Account: First, enable GuardDuty in the Master account. This account serves as the central monitoring hub.
- Invite or Automatically Include Member Accounts: Next, invite member accounts or enable auto-enrollment for new accounts. This ensures every account within the organization is continuously monitored.
- Aggregate Findings: All findings from Member accounts are sent to the Admin account, allowing security teams to prioritize threats centrally.
2. Automated Onboarding of New Accounts
Using AWS Organizations, you can configure GuardDuty to automatically include new accounts. This removes the need for manual intervention, ensuring every new AWS account is protected by GuardDuty from the start.
3. Cross-Account Visibility
A key advantage of this architecture is cross-account visibility. The Admin account gains access to all findings across accounts, which streamlines threat investigation and response efforts. GuardDuty’s cross-account support ensures consistent security monitoring across all environments.
Benefits:
- Centralized Management: Simplifies security management by having all alerts and findings consolidated in one place.
- Cost Efficiency: Allows for consolidated billing and avoids duplicating efforts across multiple accounts.
- Scalability: Automatically scales to accommodate new accounts, ensuring that security remains robust as the organization grows.
Real-World Security Scenarios with GuardDuty
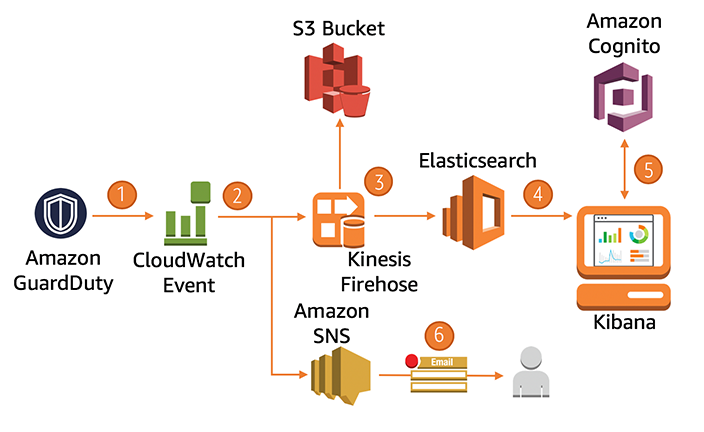
Amazon GuardDuty is built to handle a wide range of security scenarios that cloud environments face. Below are some key examples of how GuardDuty identifies and responds to different threats.
1. Detecting Cryptocurrency Mining Attacks
In a cryptocurrency attack, an attacker gains access to an EC2 instance and uses its computational resources to mine cryptocurrency (e.g., Bitcoin or Monero). This results in higher costs for the AWS account owner due to the excessive resource usage and can degrade performance for legitimate workloads.
GuardDuty’s Response:
- GuardDuty detects unusual traffic from the compromised EC2 instance to known cryptocurrency mining pools or command-and-control (C2) servers.
- It raises a finding, such as CryptoCurrency/BitcoinTool.B, which indicates suspicious activity related to cryptocurrency mining.
Automated Response:
- Use AWS Lambda to automatically isolate the compromised EC2 instance by changing its security group rules to block outbound traffic.
- Notify the security team through Amazon SNS to investigate further.
2. Detecting Unauthorized S3 Access
Attackers often target S3 buckets to exfiltrate sensitive data. GuardDuty helps identify unusual or unauthorized access patterns to S3 buckets, such as large downloads from unexpected IP addresses or regions.
GuardDuty’s Response:
- GuardDuty detects unauthorized access to S3 buckets by analyzing CloudTrail logs and DNS queries. It raises a finding like S3DataAccess, indicating that data is being accessed from an unfamiliar IP.
Automated Response:
- Trigger an AWS Lambda function that updates the bucket policy to block access from the suspicious IP or suspend the credentials being used for access.
- Log the event in AWS Security Hub for further analysis and compliance auditing.
3. Detecting Compromised EC2 Instances
Compromised EC2 instances can be used for malicious purposes, such as launching distributed denial-of-service (DDoS) attacks, running malware, or being part of a botnet.
GuardDuty’s Response:
- GuardDuty analyzes VPC Flow Logs and detects suspicious outbound traffic (e.g., connections to a known C2 server). It raises a finding like Trojan/RemoteControl, indicating the instance is compromised.
Automated Response:
- A Lambda function can be triggered to isolate the instance by updating its security group to block all outbound traffic.
- An alert is sent to the incident response team for further investigation.
4. Detecting Unusual API Activity
If an attacker gains access to AWS credentials, they might perform unauthorized actions, such as modifying IAM roles or disabling CloudTrail logging to cover their tracks.
GuardDuty’s Response:
- GuardDuty detects unusual API activity, such as disabling CloudTrail or creating new IAM users with elevated privileges. It raises findings like UnauthorizedAccess/SSHBruteForce or Policy/SuspiciousBehavior.
Automated Response:
- Use Lambda to automatically revoke the compromised API credentials and notify the security team.
- AWS Security Hub correlates the finding with other security events for a more comprehensive view of the incident.
GuardDuty Integration with AWS Services
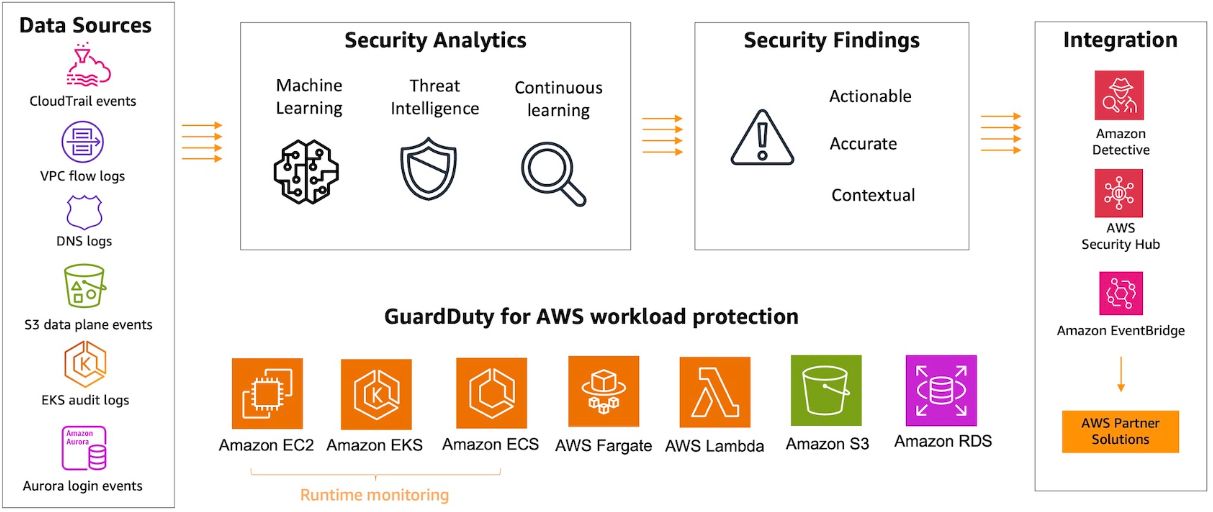
GuardDuty’s value increases when integrated with other AWS security and management tools, enabling streamlined workflows, automated responses, and deeper investigation capabilities.
1. Integration with AWS Security Hub
AWS Security Hub aggregates findings from GuardDuty, Amazon Inspector, AWS Config, and other sources. This provides a unified view of the security posture across all AWS accounts.
- Unified Dashboard: All GuardDuty findings are visible in the Security Hub dashboard, allowing security teams to prioritize and respond to threats more efficiently.
- Cross-Service Correlation: Security Hub correlates GuardDuty findings with other alerts, helping identify patterns or coordinated attacks.
2. Integration with Amazon Detective
When GuardDuty detects a threat, Amazon Detective helps investigate and understand the root cause. Detective automates the collection and analysis of log data from VPC Flow Logs, CloudTrail, and DNS logs.
- Visualizations: Detective provides visual timelines of malicious activity, showing how different AWS resources are involved.
- Historical Analysis: It allows you to explore historical events that led to the attack, helping to mitigate similar issues in the future.
3. AWS CloudWatch and Lambda
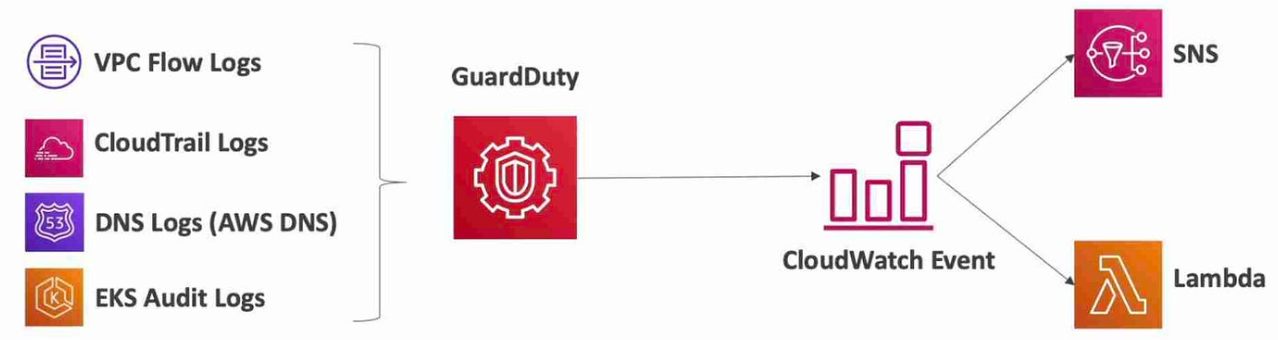
With CloudWatch, you can set up alarms based on GuardDuty findings and use Lambda for automated incident response. Common actions include:
- Automatically Quarantining Instances: When GuardDuty flags a compromised EC2 instance, a Lambda function can modify its security group or stop the instance.
- Revoking IAM Credentials: Lambda can disable compromised credentials or trigger a password reset if GuardDuty detects suspicious API activity.
GuardDuty Findings
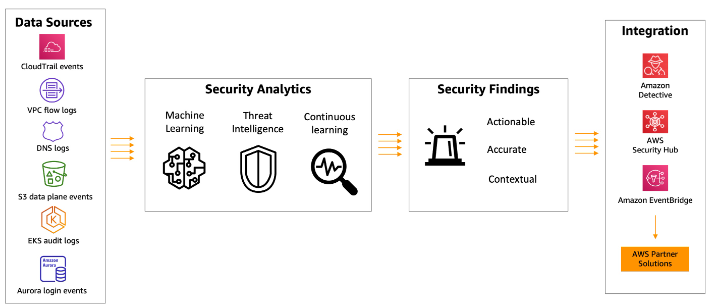
What Are GuardDuty Findings?
GuardDuty generates findings based on real-time threat detection. These findings indicate suspicious activities or potential security risks in your AWS environment, helping you quickly identify and respond to threats.
Key Components of a GuardDuty Finding
Severity:
- Low: Minor risks (e.g., reconnaissance attempts).
- Medium: Indications of unauthorized access or compromised resources.
- High: Active threats (e.g., an instance being used for malicious purposes like cryptocurrency mining).
Severity helps prioritize which findings need immediate attention.
- Type of Finding: GuardDuty categorizes findings by threat type, such as:
- Reconnaissance: Attempted scans or port probes to gather information.
- Unauthorized Access: Attempts to gain access using compromised credentials.
- Crypto-Mining: Instances being hijacked for cryptocurrency mining.
- Malware/Backdoors: Instances controlled by external attackers through trojans or remote control.
- Affected Resource: Details about the impacted resource (EC2 instance, IAM user, S3 bucket) are provided, so you know which part of your environment to investigate.
- Timestamps: Shows when the suspicious activity started and when it was last detected, giving you a timeline for the attack.
- Remediation Steps: Recommendations for addressing the issue. These may include actions like:
- Revoking compromised credentials.
- Blocking a malicious IP.
- Isolating or terminating compromised EC2 instances.
Example GuardDuty Findings
Here are some common findings with simplified explanations:
1. Recon/PortProbeUnprotectedPort
- Description: An attacker is scanning your EC2 instance for open ports.
- Severity: Low
- Action: Review security group configurations and block unnecessary ports.
2. UnauthorizedAccess/MaliciousIPCaller
- Description: A known malicious IP is using IAM credentials to access AWS resources.
- Severity: High
- Action: Immediately rotate IAM credentials and block the IP.
3. CryptoCurrency/BitcoinTool.B
- Description: An EC2 instance is being used for unauthorized cryptocurrency mining.
- Severity: High
- Action: Isolate the instance, investigate for other signs of compromise, and terminate if necessary.
Simplified Flow for Responding to Findings
- Review the Severity: Prioritize high-severity findings for immediate action.
- Examine the Affected Resource: Identify what resources (EC2, IAM, S3) are involved.
- Check the Remediation Suggestions: GuardDuty will suggest how to mitigate the issue.
- Implement Automated Responses: Use AWS services like AWS Lambda or AWS Systems Manager to automate responses based on finding severity (e.g., terminating an EC2 instance or blocking an IP address).
GuardDuty Findings and Other AWS Integrations
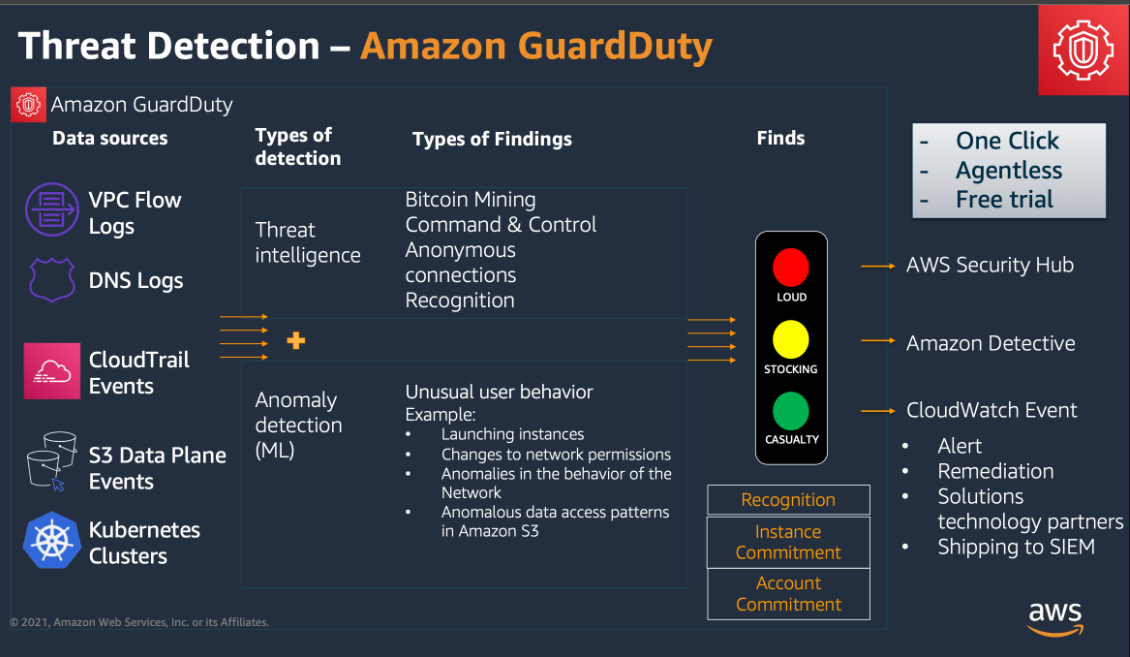
To get the most out of GuardDuty findings, you can integrate with other AWS services like:
- AWS Security Hub: Centralized view of all security findings, including GuardDuty, for better management.
- Amazon Detective: Provides deeper investigation into the root causes of GuardDuty findings.
- AWS Lambda: Automates remediation by triggering Lambda functions to respond to threats (e.g., revoking credentials or stopping instances).
Best Practices and Architectural Patterns
Building an efficient security framework with GuardDuty requires adopting certain architectural patterns to handle real-time threats and protect critical AWS resources.
1. Centralized Security Monitoring in Multi-Account Environments
This pattern involves using a centralized Admin account to monitor GuardDuty findings from multiple Member accounts. It’s ideal for large organizations with distinct environments (e.g., production, dev, test) under separate accounts.
- Pattern: Configure GuardDuty in a centralized account, forward all findings to a Security Operations Center (SOC) team, and automate incident responses across accounts.
2. Automated Incident Response Framework
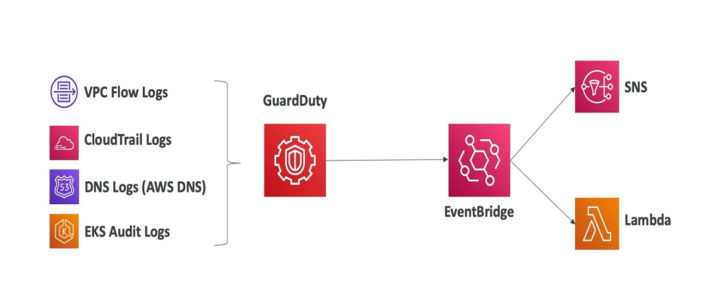
For faster incident resolution, automate responses to specific GuardDuty findings by integrating AWS Lambda, Amazon CloudWatch, and AWS Systems Manager. Define clear workflows for common threats (e.g., compromised EC2, unusual S3 access) and automatically trigger remediation actions.
3. Combining GuardDuty with IAM and VPC Security Controls
GuardDuty works best when combined with robust Identity and Access Management (IAM) and VPC network security configurations. Ensure least privilege access policies for all users, roles, and services, and use VPC Flow Logs to monitor network traffic patterns.
Conclusion
Amazon GuardDuty is a powerful tool that enables continuous, real-time threat detection in AWS environments. By leveraging machine learning, anomaly detection, and third-party threat intelligence, it helps secure your AWS accounts from a wide variety of threats, from compromised EC2 instances to unauthorized S3 access.
For security professionals and cloud engineers alike, integrating GuardDuty with other AWS services such as Security Hub, Detective, CloudWatch, and Lambda unlocks even more value, enabling centralized monitoring, automated incident responses, and efficient root cause analysis.
Whether you're managing a single AWS account or a sprawling multi-account enterprise setup, GuardDuty should be an integral part of your cloud security strategy. As cyber threats evolve, GuardDuty’s continuous learning and threat intelligence updates ensure your cloud environment stays secure, providing peace of mind in an increasingly connected world.
By adopting best practices and leveraging GuardDuty’s advanced features, you can build a comprehensive, scalable security framework that keeps pace with the dynamic nature of cloud computing.
Happy Clouding!!!
Did you like this post?
If you did, please buy me coffee 😊
Nicely written
Yeah